Cybersecurity Services
In today's digital age which is dominated by technology, cyber security is not a choice any more it is a must for business continuity and trust. At eCorpIT we put forth full scale cyber security solutions which we tailor to protect your data, systems and operations from the ever growing cyber threats and regulatory issues. As a proven player in the cyber security field we take a proactive approach to security. We have a team of experts who do a security assessment, real time threat monitoring and put in place multi-layer defence strategies which in turn reduce risk without putting a dent in day to day operations. Through our cyber security consulting we help organizations to understand their security status, we also help them to comply with regulatory requirements and in the process we help them to build a strong base for the future.
With our managed cybersecurity solutions, your infrastructure will be protected 24/7 by our incident response, threat detection, and monitoring services. We craft tailored solutions that evolve with advancing threats, whether it be network and cloud security, identity management, or data protection. Cybersecurity threats are integrated within your business strategy at eCorpIT. We create secure, resilient, and compliant environments that safeguard your reputation and support growth. Confidence will be provided to you in an ever changing complex digital environment.
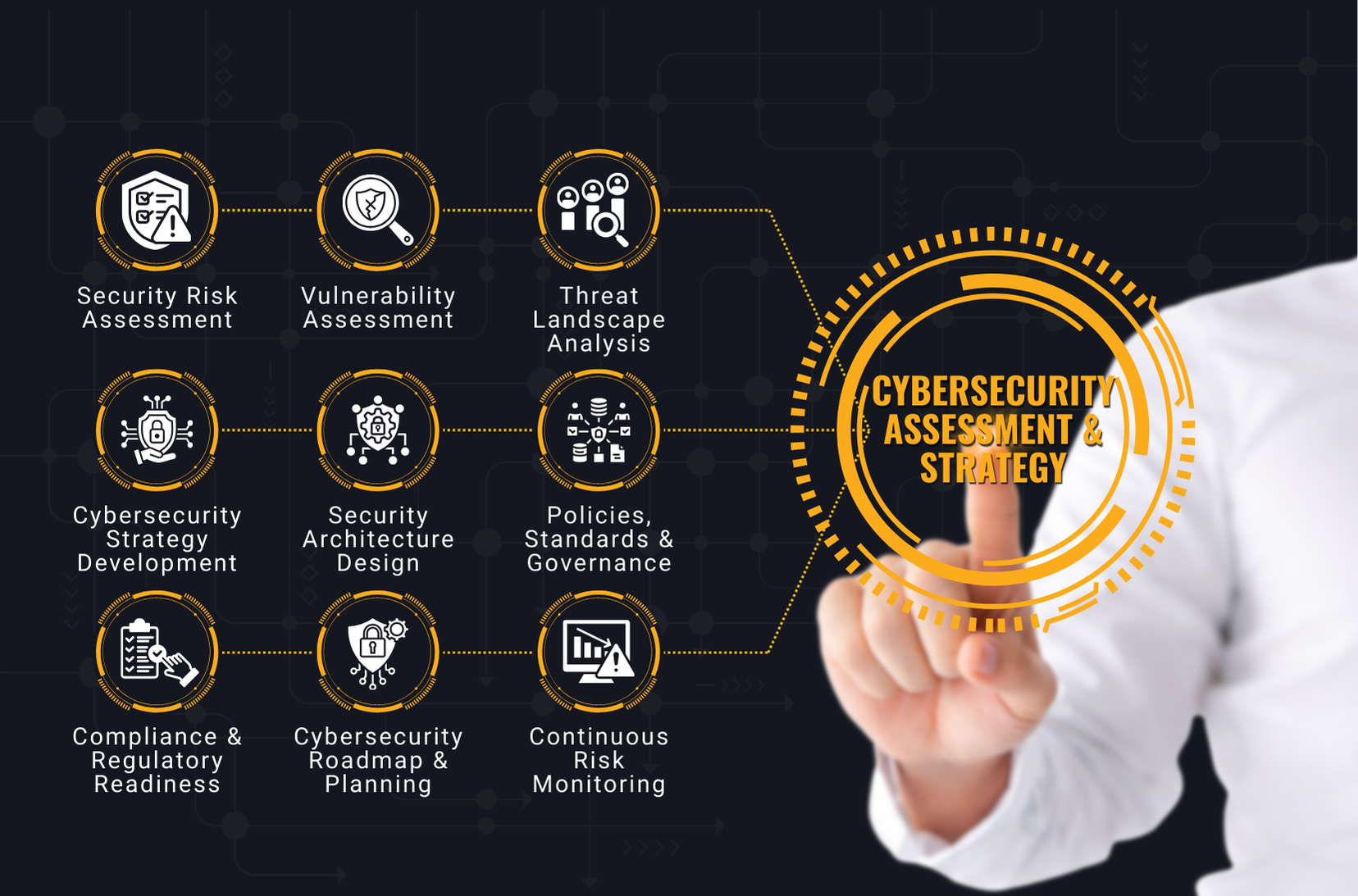
Cybersecurity Assessment & Strategy
- Security posture evaluation
- Risk & gap analysis
- Compliance and regulatory advisory (GDPR, HIPAA, ISO, PCI-DSS)
- Security architecture & roadmap planning
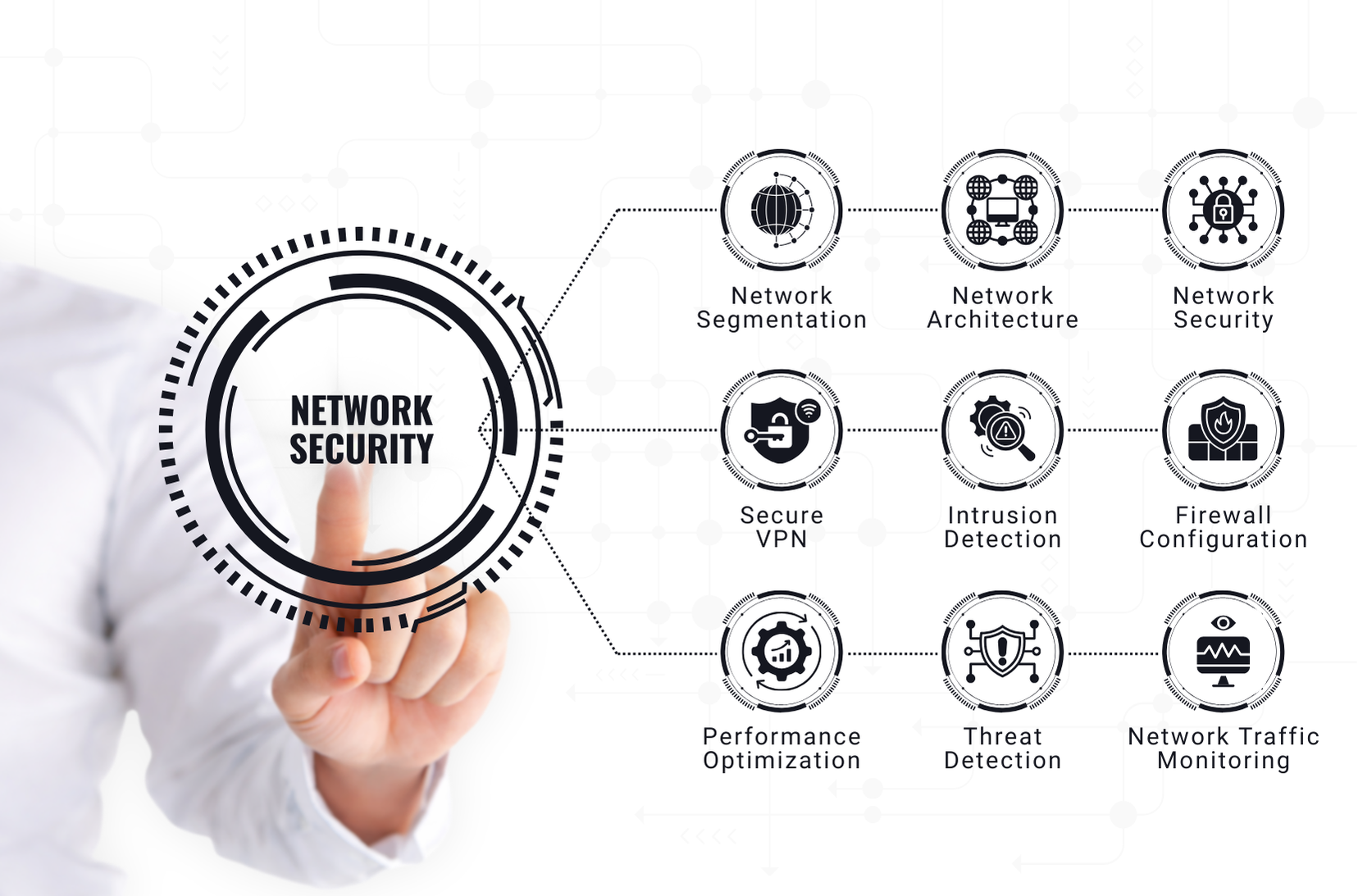
Network Security
- Firewall and intrusion detection systems (IDS/IPS)
- Network segmentation and monitoring
- VPN and secure remote access
- Zero Trust Architecture
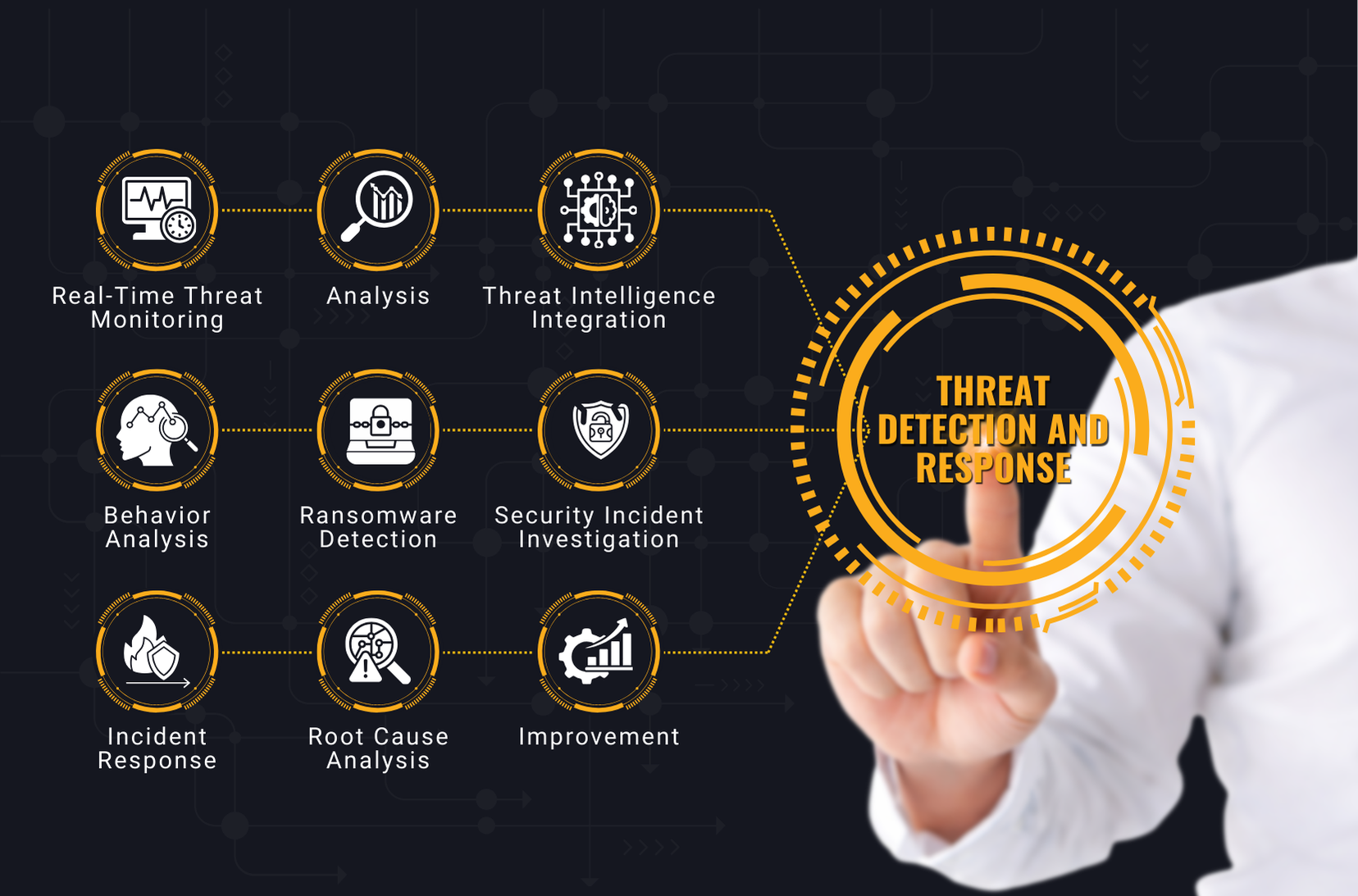
Threat Detection and Response
- 24/7 Security Operations Center (SOC)
- SIEM implementation and management
- Endpoint Detection & Response (EDR)
- Incident response and forensics
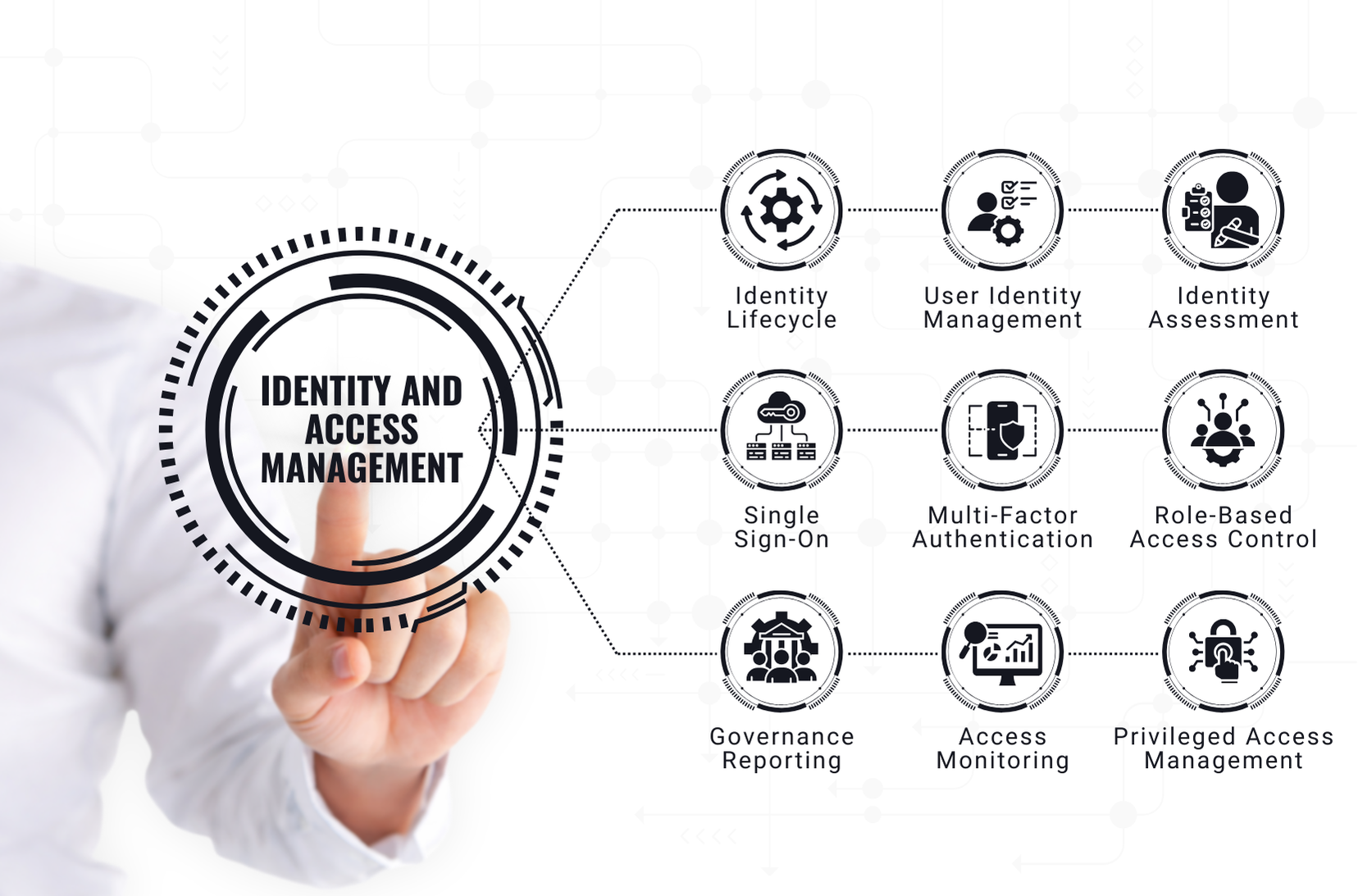
Identity and Access Management
- Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
- Role-based access controls
- Privileged access management
- Identity governance
Data Encryption and Protection
- End-to-end data encryption (at rest & in transit)
- Secure backup and disaster recovery
- Data loss prevention (DLP) policies
- Cloud data protection and compliance controls
Application Security
- Web and mobile application security testing (VAPT)
- Secure DevOps (DevSecOps) integration
- Code review and vulnerability scanning
- OWASP Top 10 mitigation
Why Choose eCorpIT for Cybersecurity?
Drop Us a Message
Ready to Transform Your Business?
Let’s craft a custom roadmap that delivers measurable ROI and sustainable innovation.
👉 Schedule Your Free Consultation
